Cara mengamankan infrastruktur Anda dengan Cloudflare Zero Trust telah menjadi topik yang semakin penting di era kerja jarak jauh, ancaman siber yang terus berkembang, dan lingkungan TI yang kompleks. Model keamanan berbasis perimeter tradisional tidak lagi memadai. Organisasi beralih ke model di mana akses tidak pernah diberikan secara otomatis, bahkan kepada pengguna di dalam jaringan.
Cloudflare Zero Trust menyediakan solusi yang skalabel dan andal yang memungkinkan bisnis menerapkan kontrol akses berbasis identitas, melindungi sumber daya internal, dan memungkinkan akses jarak jauh yang aman tanpa bergantung pada VPN lama. Artikel ini akan memandu Anda mempelajari dasar-dasar Cloudflare Zero Trust, cara kerjanya, dan cara penerapannya yang efektif, baik untuk tim kecil maupun perusahaan besar.
Daftar isi
BeralihApa itu Cloudflare Zero Trust?
Cloudflare Zero Trust adalah kerangka kerja keamanan modern yang dirancang untuk memverifikasi setiap pengguna, perangkat, dan permintaan, terlepas dari lokasi jaringan mereka, sebelum memberikan akses ke sumber daya apa pun. Pendekatan ini menggantikan model berbasis perimeter yang sudah ketinggalan zaman dengan arsitektur berbasis identitas yang secara signifikan mengurangi risiko pelanggaran dan membatasi paparan ancaman internal.
Jika Anda bertanya-tanya bagaimana cara mengamankan dengan Cloudflare Zero Trust, jawabannya terletak pada prinsip intinya: tidak mempercayai siapa pun secara default. Setiap upaya akses harus memenuhi persyaratan autentikasi, otorisasi, dan postur perangkat yang ketat. Hal ini memastikan bahwa bahkan pengguna internal diperlakukan dengan pengawasan yang sama seperti koneksi eksternal, menciptakan lingkungan yang konsisten dan aman di semua titik akhir dan layanan.
Fitur Inti:
Kebijakan akses tingkat aplikasi
Akses jarak jauh yang aman tanpa VPN
Kontrol akses berbasis identitas (Google, Azure AD, GitHub, dll.)
Penegakan postur perangkat (versi OS, antivirus, dll.)
Pencatatan dan analitik lalu lintas
Integrasi yang mulus dengan infrastruktur yang ada
Mengapa Menggunakan Zero Trust?
Organisasi modern seringkali mengandalkan tenaga kerja hibrida dan lingkungan multi-cloud. Model keamanan tradisional yang mengandalkan apa pun di dalam jaringan tidak lagi mampu menangani dinamika pengguna dan ancaman. Zero Trust membantu:
Mencegah pergerakan lateral yang tidak sah
Minimalkan penyalahgunaan kredensial
Meningkatkan visibilitas dan kepatuhan akses
Hilangkan ketergantungan pada firewall perimeter yang rapuh
Ikhtisar Arsitektur Cloudflare Zero Trust
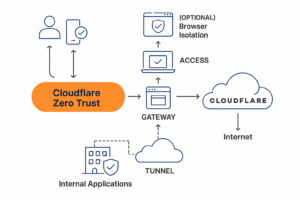
Platform Zero Trust Cloudflare menggabungkan beberapa komponen penting:
Mengakses: Kontrol akses ke aplikasi internal atau pribadi
Gerbang:Lindungi perangkat dengan memfilter lalu lintas DNS dan HTTP
Terowongan: Mengekspos layanan ke internet dengan aman tanpa membuka port
Isolasi Peramban (opsional): Render situs web dari jarak jauh untuk perlindungan ekstra
Semua lalu lintas melewati tepi global Cloudflare, menerapkan aturan Zero Trust secara konsisten, terlepas dari lokasi pengguna.
Langkah demi Langkah: Menyiapkan Cloudflare Zero Trust
1. Buat Akun Cloudflare dan Aktifkan Zero Trust
Mulailah dengan mendaftar di portal resmi Cloudflare Zero Trust:
https://developers.cloudflare.com/cloudflare-one
Setelah registrasi:
Tetapkan nama organisasi Anda
Verifikasi email Anda
Siapkan penyedia identitas Anda
2. Tambahkan Domain dan Rutekan Lalu Lintas Anda
Untuk mengamankan aplikasi, domain Anda harus dikelola melalui Cloudflare:
Masuk ke https://dash.cloudflare.com
Tambahkan domain Anda
Ubah catatan DNS Anda agar mengarah ke nameserver Cloudflare
Setelah DNS aktif, semua lalu lintas dapat disaring dan dilindungi oleh Cloudflare.
3. Terapkan Terowongan Cloudflare
Cloudflare Tunnel (sebelumnya Argo Tunnel) memungkinkan Anda mengekspos layanan internal tanpa membuka port firewall.
wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-amd64.deb sudo dpkg -i cloudflared-linux-amd64.deb login terowongan cloudflared buat terowongan cloudflared aplikasi internal
Kemudian konfigurasikan terowongan Anda:
# /etc/cloudflared/config.yml terowongan: file kredensial aplikasi internal: /root/.cloudflared/internal-app.json masuk: - nama host: app.example.com layanan: http://localhost: - layanan: http_status:404
Luncurkan terowongan:
rute terowongan cloudflared dns aplikasi-internal app.example.com terowongan cloudflared jalankan aplikasi-internal
Layanan internal Anda sekarang dapat diakses dengan aman melalui https://app.example.com
4. Konfigurasikan Kebijakan Akses
Setelah terowongan berjalan, Anda dapat melindunginya dengan kebijakan Akses:
Pergi ke Akses > Aplikasi
Klik Tambahkan aplikasi
Memilih Dihosting sendiri
Tentukan aturan (misalnya, hanya pengguna dengan
@perusahaan.comdomain)Secara opsional terapkan MFA, akses berbasis negara, atau pemeriksaan perangkat
Log akses dan pemantauan pengguna secara real-time tersedia di dasbor.
Kasus Penggunaan di Dunia Nyata
Alat Internal yang Aman:Lindungi panel admin, lingkungan pengembangan, dan situs pementasan dari akses tidak sah
Pemberdayaan Tim Jarak Jauh: Izinkan akses aman ke aplikasi tanpa mengeksposnya secara publik atau bergantung pada VPN lama
Peningkatan Kepatuhan: Terapkan pemeriksaan perangkat dan SSO agar sesuai dengan peraturan industri (SOC 2, ISO 27001)
Pencatatan dan Pemantauan
Cloudflare Zero Trust menawarkan kemampuan observasi penuh atas peristiwa akses, identitas pengguna, dan perilaku sesi. Log dapat dikirimkan ke alat pihak ketiga seperti:
AWS S3
Splunk
Anjing Data
Platform SIEM
Dokumentasi: https://developers.cloudflare.com/logs
Praktik Terbaik
Gunakan akses berbasis identitas daripada IP statis
Terapkan MFA pada semua aplikasi
Audit aturan akses dan paparan aplikasi secara berkala
Terapkan validasi postur perangkat
Pantau log dan integrasikan dengan SIEM Anda untuk peringatan waktu nyata
Mencari Infrastruktur Terkelola?
Jika Anda berencana untuk menerapkan Cloudflare Zero Trust tetapi juga membutuhkan infrastruktur cloud yang andal atau hosting VPS terkelola untuk menjalankan aplikasi Anda, Quape menawarkan solusi yang dapat disesuaikan yang selaras sempurna dengan prinsip Zero Trust.
Apakah Anda membutuhkan:
Hosting cloud yang aman
Paparan aplikasi tanpa VPN khusus
Lingkungan akses jarak jauh
VPS berkinerja tinggi dengan aturan jaringan khusus
Semua itu tersedia di Hosting VPSTim teknis Quape dapat membantu Anda dengan pengaturan Cloudflare, integrasi terowongan, dan penerapan aman yang disesuaikan dengan kasus penggunaan Anda.
Dari tim startup hingga lingkungan perusahaan, Quape menyediakan fondasi yang mulus untuk menerapkan praktik keamanan modern seperti Cloudflare Zero Trust tanpa mengorbankan kecepatan atau fleksibilitas.
Pikiran Akhir
Transisi ke model Zero Trust bukan sekadar peningkatan keamanan, melainkan evolusi yang diperlukan untuk infrastruktur modern. Cloudflare Zero Trust menawarkan pendekatan yang efisien, skalabel, dan berbasis identitas untuk mengamankan aplikasi, data, dan tim Anda. Dikombinasikan dengan dukungan hosting dan infrastruktur yang tangguh dari platform seperti Quape, membangun lingkungan Zero Trust tidak pernah semudah ini.
Jelajahi pilihan Anda hari ini, dan ambil langkah berikutnya menuju masa depan yang aman dan fleksibel.
- Gangguan Cloudflare? Insiden November 2025 - 18 November 2025
- CVE-2025-11953 Cacat Keamanan CLI React Native yang Kritis - 7 November 2025
- Cara Menyebarkan n8n di Ubuntu 24.04 - 4 November 2025



